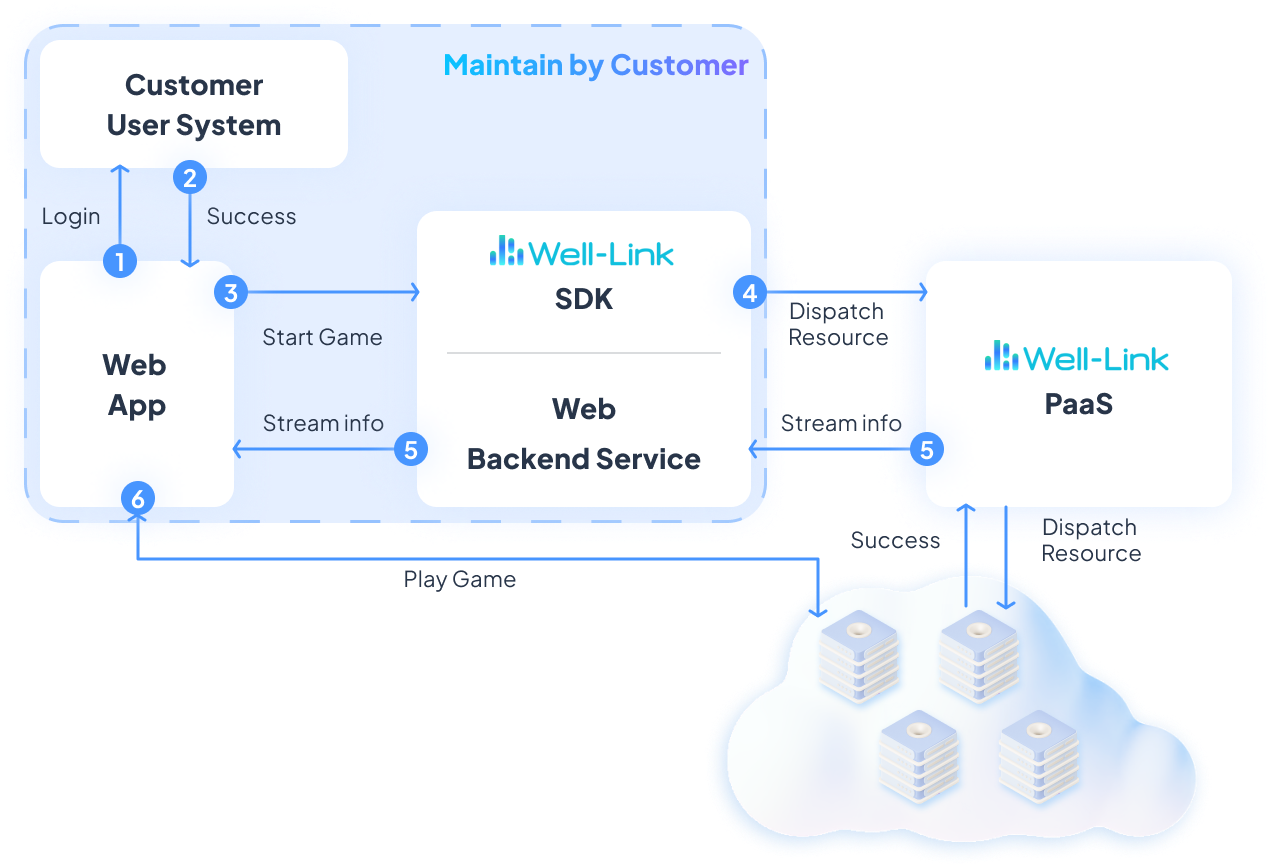
What is Well-Link's cloud rendering/cloud gaming solution?
Well-Link provides industry-leading cloud rendering and cloud gaming solutions. Our technology processes high-demand 3D rendering and game computing in the cloud, streaming it to user devices through advanced streaming technology, enabling high-quality gaming experiences on any device.
How to start using Well-Link's services?
Simply contact us and submit your game package with specific requirements to begin the integration process.
What are the billing options for Well-Link's services?
We offer flexible billing plans including reserved instances (by month/year), daily-based billing (on-demand/pay-as-you-go), and custom solutions for specific business needs.
Does your service support access control features?
Yes, we provide IP whitelisting functionality for access control. This allows you to restrict service access to specific IP addresses, enhancing your account security.
Is data transmission encrypted?
Absolutely. We prioritize the security of your data at all times. All communication is protected with industry-standard encryption protocols.
How does your service handle user account information and authentication?
Our service is designed to integrate seamlessly with your existing authentication system. We do not maintain or store user account information ourselves. Instead, we rely on your authentication service to manage all aspects of user accounts and access. This approach allows you to maintain full control over your users' data and security policies.
Specifically:
1. User Authentication: Users log in through your authentication service. We do not store or manage user credentials.
2. Account Policies: All account policies, including password requirements, multi-factor authentication (MFA), single sign-on (SSO), account lockout rules, and password change prompts, are managed entirely by your authentication system.
3. Administrative Control: Your administrators have full control over all authentication policies and user management through your own systems.
4. Personal Information Management: As we don't store personal user information, the management of such data remains under your control and policies.
5. Responsibility in Case of Data Breach: In the event of a credential leak, the responsibility would typically lie with the party managing the authentication system (in this case, your organization). However, specific responsibilities would be outlined in our service agreement.
This structure allows you to maintain your existing security protocols and compliance measures while using our service. If you have any specific security requirements or concerns, we're happy to discuss how our service can best integrate with your authentication system.
In case of ID/password or other sensitive information leakage, do you have a mechanism to immediately suspend services as an initial response?
Yes, we can suspend services in such cases. This process requires technical cooperation between our team and your team to ensure a smooth and secure response.
Is there an automatic logout feature for inactive sessions?
Yes, we have implemented a session timeout feature. If there's no activity for 2 minutes, the user will be automatically logged out.
Do you maintain access logs and usage history? Can administrators view these records?
We retain certain logs for operational purposes, primarily for troubleshooting and issue resolution. These logs are used internally to address technical concerns when necessary.
Do you have operational manuals for log management and access?
Yes, we can provide relevant manuals for log management and access procedures based on your specific requirements.
How do you manage access control for logs and usage data within your operational team?
We strictly manage access permissions to logs and usage data based on roles within our company. This ensures that only authorized personnel can access sensitive information, and only when necessary for their job functions.
Do you have mechanisms to detect and prevent unauthorized access and network attacks?
Yes, we have robust security measures in place. Additionally, our cloud service provider implements their own intrusion detection mechanisms, providing an extra layer of security.
Do you have rules and operational manuals for security updates? Are these updates performed according to these guidelines?
We follow the cloud security baseline defined by Microsoft for our security operations. You can find more details about these standards at: https://learn.microsoft.com/en-us/security/benchmark/azure/overview
Do your contracts, terms of service, and usage policies include clauses prohibiting the misuse of information and disclosure to third parties?
Yes, our contracts include specific clauses addressing data protection, prohibiting unauthorized use of information and disclosure to third parties.
If the service uses AI technology, is user input data used for AI training?
Our AI services do not use customer data for training purposes. We prioritize data privacy and security.
In case of emergencies such as system failures or network attacks, do you have a recovery/restoration environment and system in place?
We can provide recovery capabilities based on your specific needs, including regional considerations and scale requirements.
Has your company obtained public certifications such as ISO/IEC 27000 series, SOC1~3, or P-mark? If certified, please provide a URL where we can confirm the certification number and other information.
These certifications typically apply to the infrastructure level, which is managed by our cloud provider. For example, for Azure, please refer to https://learn.microsoft.com/en-us/azure/compliance/ for information on their certifications and compliance standards.